AWS Lambda is a serverless compute service that lets you seamlessly run any application code or service without managing or provisioning servers.
RudderStack supports AWS Lambda as a destination where you can send your event data seamlessly.
Getting started
Before configuring AWS Lambda as a destination in RudderStack, verify if the source platform is supported by AWS Lambda by referring to the table below:
| Connection Mode | Web | Mobile | Server |
|---|---|---|---|
| Device mode | - | - | - |
| Cloud mode | Supported | Supported | Supported |
Once you have confirmed that the source platform supports sending events to AWS Lambda, follow these steps:
- From your RudderStack dashboard, add the source. Then, from the list of destinations, select AWS Lambda.
- Assign a name to the destination and click Continue.
Connection settings
To successfully configure AWS Lambda as a destination, you need to configure the following settings:
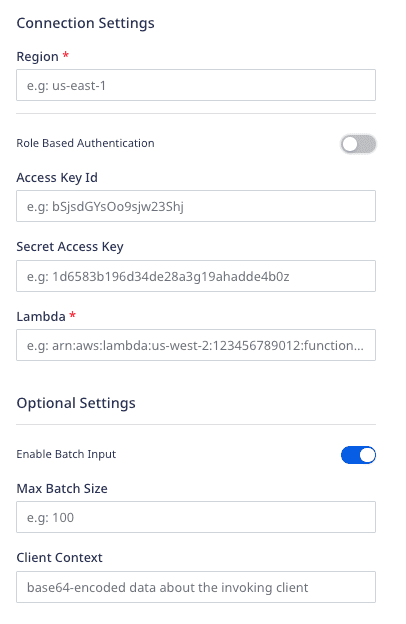
- Region: Enter the region associated with your AWS Lambda service.
Role Based Authentication: Enable this setting to use role-based AWS authentication for this destination.
When disabled, you need to configure the following settings:
- Access Key ID: Enter the AWS access key ID associated with your IAM user account.
- Secret Access Key: Enter your secret access key.
When enabled, you need to configure the following settings:
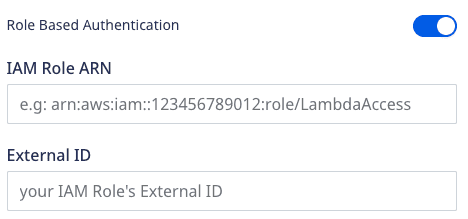
- IAM Role ARN: Enter your role ARN. For more information on the IAM ARNs, refer to the AWS documentation.
For more information on creating an IAM role in AWS, refer to the AWS documentation.- External ID: Enter the external ID used to create the IAM role. For more information on using the external ID, refer to the AWS documentation.
It is highly recommended to use the workspace token as the external ID while creating the IAM role, as AWS recommends that the external ID should be domain-specific.Lambda: Enter the name of the Lambda function to be invoked. RudderStack supports the following formats:
| Name format | Example |
|---|---|
| Function name |
|
| Function ARN | arn:aws:lambda:us-west-2:123456789012:function:my-function |
| Partial ARN | 123456789012:function:lambda-function |
- Enable Batch Input: Enable this setting if your lambda function expects a batch input (array of events) in the event object.
- Max Batch Size: If Enable Batch Input setting is enabled, use this field to set the maximum size of the event batch.
- Client Context: Use this field to pass up to 3583 bytes of Base64-encoded data about the invoking client to the function in the context object.
Supported events
You can send your identify, track, page, group, and alias events to your lambda function via RudderStack.
RudderStack leverages the AWS SDK for Go to send the events to the lambda function. It uses the SDK's Invoke method to asynchronously invoke the lambda function.
Viewing error logs
RudderStack does not get any information related to the runtime errors for your lambda function. As a result, you will not be able to view these errors in the Live Events tab of your dashboard.
To view these errors, you can configure the AWS CloudWatch logs for your lambda function.
FAQ
Why am I getting a UnrecognizedClientException/InvalidSignatureException error?
If you're getting a UnrecognizedClientException error with a 403 status code, verify if your AWS credentials (both AWS Access Key ID and Secret Access Key) are valid.
For the InvalidSignatureException error, verify if the provided secret access key is valid.
Contact us
For more information on the topics covered on this page, email us or start a conversation in our Slack community.